AD Privilege Discovery
Using the data set contained in this SANS Slingshot Linux image, find a reliable path from a Kerberoastable user to the Domain Admins group. What’s the user’s logon name? Remember to avoid RDP as a control path as it depends on separate local privilege escalation flaws.
For hints on achieving this objective, please visit Holly Evergreen and help her with the CURLing Master Cranberry Pi terminal challenge.

Bloodhound Demo hint from
Bloodhound Demo
Bloodhound Tool hint from
Bloodhound Tool
Have you ever used Bloodhound for testing Active Directory implementations?
It's a merry little tool that can sniff AD and find paths to reaching privileged status on specific machines.
AD implementations can get so complicated that administrators may not even know what paths they've set up that attackers might exploit.
Have you seen anyone demo the tool before?
Download SANS Slingshot Linux image and run it in VMWare WorkStation Player.
Run Bloodhound from Desktop.
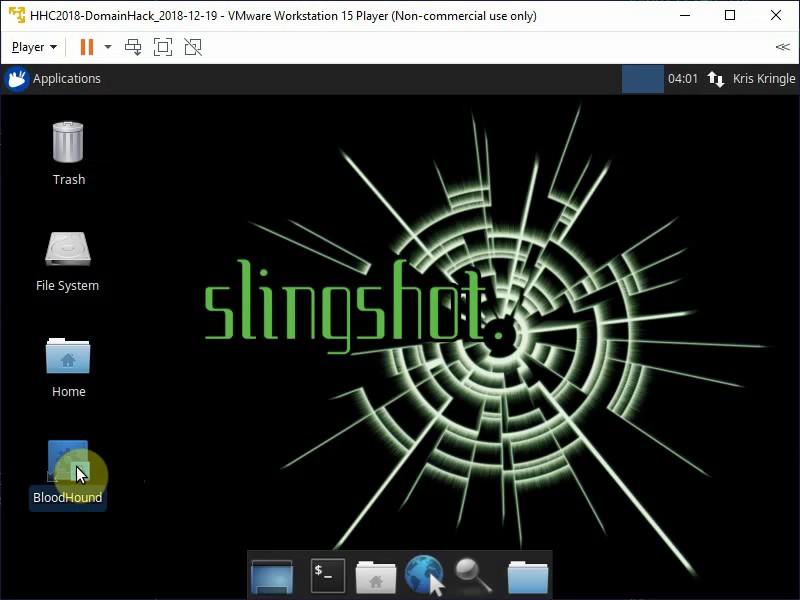
Select from pre-defined queries Shortest path to Domain Admins from Kerberoastable Users.
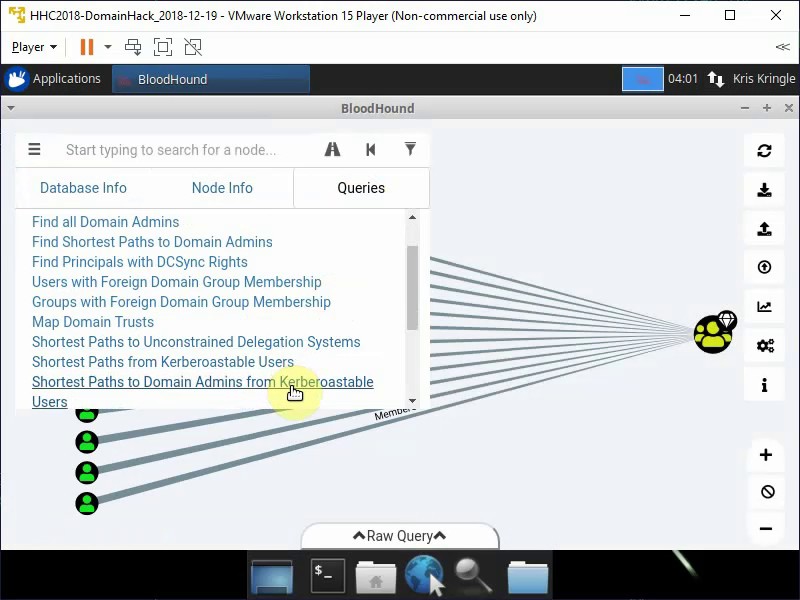
Check the paths from Domain Admins to exclude paths, which has RDP as a control path (CanRDP).
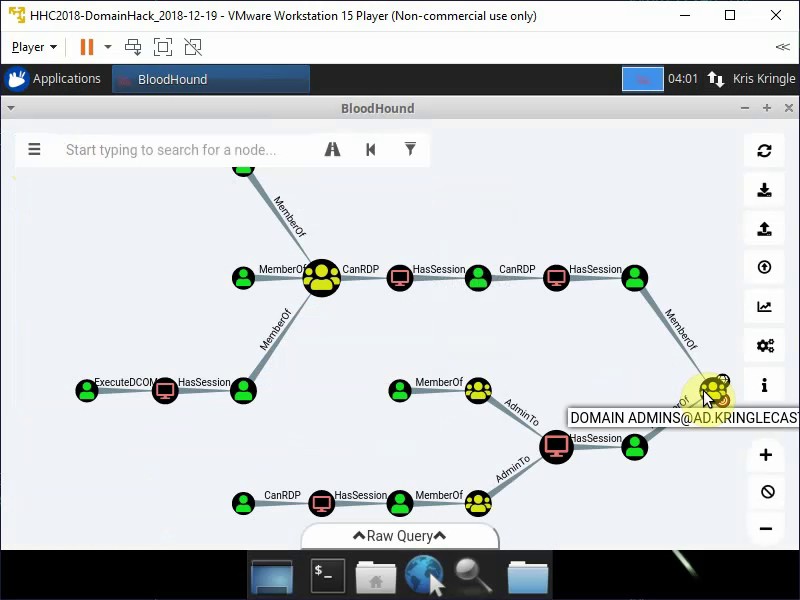
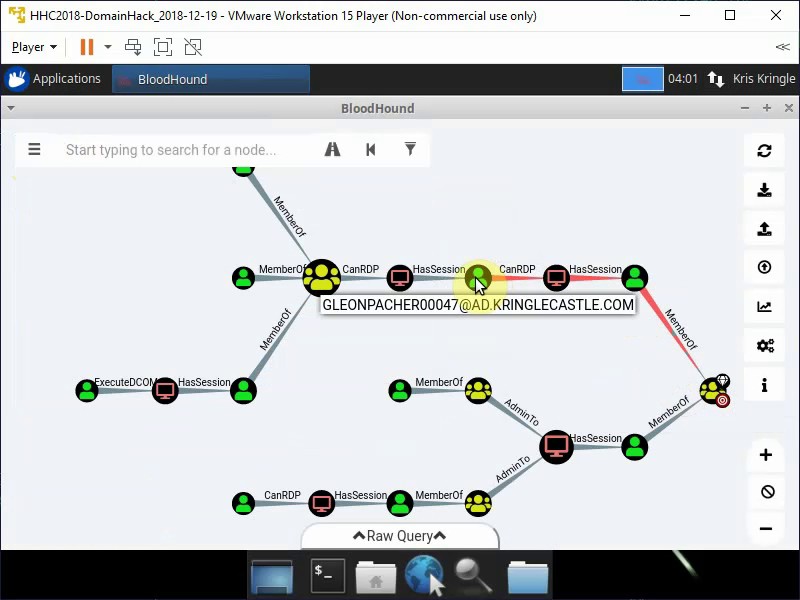
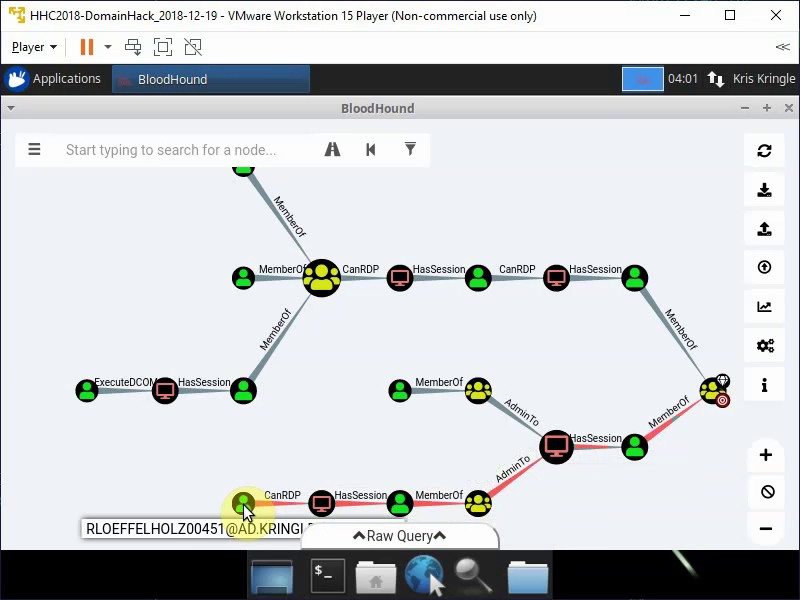
Only one valid path is left.
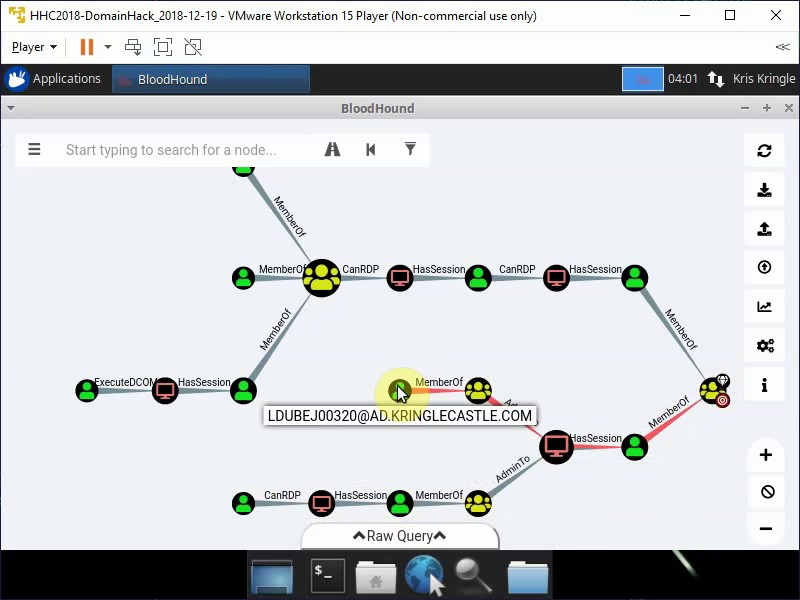
Answer to this objective is LDUBEJ00320@AD.KRINGLECASTLE.COM.