DNS Records (gold, 200p)
Security researcher was inspecting traffic from compromised network.
Reviewing http, https, imap and ssh packets he was not able to find anything suspicious.
But after discussions with other security researchers, he decided to inspect DNS traffic.
To his surprise DNS requests and responses had very interesting artifacts from 2020.cboe DNS zone.
Try to find the flag from DNS server 10.1XX.1YY.113
Can you find the flag from DNS server?
solution
First let's ask for SOA record, containing administrative information about the zone, both with dig and nslookup for readability.
Nothing interesting.
$ dig -t soa 2020.cboe @10.1XX.1YY.113 +short
ns.2020.cboe. root.2020.cboe. 29 604800 86400 2419200 604800$ nslookup -q=SOA 2020.cboe 10.1XX.1YY.113
Server: 10.1XX.1YY.113
Address: 10.1XX.1YY.113#53
2020.cboe
origin = ns.2020.cboe
mail addr = root.2020.cboe
serial = 29
refresh = 604800
retry = 86400
expire = 2419200
minimum = 604800
Looking up DNS server software and hostname. It's running pretty recent bind 9.16.1 DNS server on Ubuntu. Nothing interesting.
$ dig -t txt -c chaos version.bind @10.1XX.1YY.113 +short
"9.16.1-Ubuntu"
$ dig -t txt -c chaos hostname.bind @10.1XX.1YY.113 +short
"3e1087efdd60"
Trying DNS zone transfer with AXFR record, didn't work, because port 53/tcp is closed.
Even if it was open, I doubt that it would be misconfigured this way, but it's worth to check.
$ dig axfr 2020.cboe @10.1XX.1YY.113
;; Connection to 10.1XX.1YY.113#53(10.1XX.1YY.113) for 2020.cboe failed: connection refused.
Looking up common DNS records - A, AAAA, MX, TXT, etc. also didn't yield to anything.
Running a DNS subdomain enumeration with gobuster shows multiple subdomains.
But none of them contain any other DNS record than A, which is useless.
$ gobuster dns -i -d 2020.cboe -r 10.1XX.1YY.113 -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
Found: webmail.2020.cboe [10.30.10.12]
Found: ftp.2020.cboe [10.20.30.10]
Found: www.2020.cboe [10.20.10.13]
Found: w.2020.cboe [10.20.10.11]
Found: server.2020.cboe [10.10.10.1]
Found: pop.2020.cboe [10.20.10.13]
Found: ns.2020.cboe [127.0.0.1]
Found: ww.2020.cboe [10.20.10.12]
Found: smtp.2020.cboe [10.20.10.13]
Found: owa.2020.cboe [10.30.10.11]
Found: imap.2020.cboe [10.20.10.13]
Found: relay.2020.cboe [10.20.10.13]
Found: wwww.2020.cboe [10.20.10.14]
Found: server2.2020.cboe [10.10.10.20]
Found: server1.2020.cboe [10.10.10.10]
Found: server3.2020.cboe [10.10.10.30]
Running a DNS subdomain enumeration with fierce shows same multiple subdomains found previously.
$ fierce --domain 2020.cboe --subdomain-file /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --dns-server 10.1XX.1YY.113
NS: ns.2020.cboe.
SOA: ns.2020.cboe. (127.0.0.1)
Zone: failure
Wildcard: failure
Found: www.2020.cboe. (10.20.10.13)
Found: ftp.2020.cboe. (10.20.30.10)
Found: webmail.2020.cboe. (10.30.10.12)
Found: smtp.2020.cboe. (10.20.10.13)
Found: pop.2020.cboe. (10.20.10.13)
Found: ns.2020.cboe. (127.0.0.1)
Nearby:
{'127.0.0.1': 'localhost.'}
Found: imap.2020.cboe. (10.20.10.13)
Found: server.2020.cboe. (10.10.10.1)
Found: owa.2020.cboe. (10.30.10.11)
Found: relay.2020.cboe. (10.20.10.13)
Found: server1.2020.cboe. (10.10.10.10)
Found: server2.2020.cboe. (10.10.10.20)
Found: ww.2020.cboe. (10.20.10.12)
Found: server3.2020.cboe. (10.10.10.30)
Found: wwww.2020.cboe. (10.20.10.14)
Found: w.2020.cboe. (10.20.10.11)
Finally, running a DNS subdomain enumeration with massdns shows multiple CNAME records from 1 to 42.
$ git clone https://github.com/blechschmidt/massdns
$ cd massdns
$ make
mkdir -p bin
cc -O3 -std=c11 -DHAVE_EPOLL -DHAVE_SYSINFO -Wall -fstack-protector-strong src/main.c -o bin/massdns
$ echo "10.1XX.1YY.113" > resolver.txt
$ python3 ./scripts/subbrute.py lists/names.txt 2020.cboe | ./bin/massdns -r resolver.txt -q -o S
www.2020.cboe. A 10.20.10.13
4.2020.cboe. CNAME ff1ffe6b480b10b38dd9878e68a974b8.<shortened output>.9219d0a54662a4bcd80b9edbdbdf59e5.2020.cboe.
1.2020.cboe. CNAME 1f8b08000311a95f0003ed97e9371b08.<shortened output>.fb4ed1242a53a176aad624d508498825.2020.cboe.
w.2020.cboe. A 10.20.10.11
5.2020.cboe. CNAME c14bcae90b4cc1d15bd4f241e27628ca.<shortened output>.43c9fb25d0fbc167eb4cdc6df4b615b1.2020.cboe.
7.2020.cboe. CNAME ffca2f0cb9f4ae1a47b689490c5cf96b.<shortened output>.58cc6c30a5f8efd77364dad9072b1c43.2020.cboe.
9.2020.cboe. CNAME 549dadccdddbabc663f7f15bbdc30166.<shortened output>.d3c3f0bfe6d95b7208ece8069e54d0e9.2020.cboe.
relay.2020.cboe. CNAME www.2020.cboe.
2.2020.cboe. CNAME 8b88044ffb2f3caf7e2f9e17f773eff7.<shortened output>.647f1547e1d68ed6004073b6acd4ef87.2020.cboe.
17.2020.cboe. CNAME efd14601bbeb26a8990bdaae24a8eaf4.<shortened output>.afbce0df54537705410d46a61326670a.2020.cboe.
ns.2020.cboe. A 127.0.0.1
owa.2020.cboe. A 10.30.10.11
ww.2020.cboe. A 10.20.10.12
13.2020.cboe. CNAME ef3b87e696590c749dd9f30e61872054.<shortened output>.063518ce979769468f6deea20a833235.2020.cboe.
12.2020.cboe. CNAME 965d72e7a6f85eda8308ca3f4e0ddd61.<shortened output>.9f22d5cfa19fa36e0a9f96e7bf1bb83a.2020.cboe.
15.2020.cboe. CNAME 59fca8aca48a6ae994214d0c86c683b7.<shortened output>.27bf5a60813b5e06a8f56eefd9114472.2020.cboe.
14.2020.cboe. CNAME d5465517c5ad6b4dc20db0b49948f44f.<shortened output>.8f4ce7d1e8571ed9b56e9a08af39bf6b.2020.cboe.
16.2020.cboe. CNAME f0bc85a4a832fe3493c9886931d1eb82.<shortened output>.3478e9faf0963c9206c4cb4cbea9d64d.2020.cboe.
19.2020.cboe. CNAME 03789f749c4349ffc8640f77723b4522.<shortened output>.cc854ec4f32df5732a690fb9d61b9f5c.2020.cboe.
18.2020.cboe. CNAME 0f5417bd2983ca62e92841ae562bcee1.<shortened output>.a0baacb3225bff55f7607d8a63c4ceef.2020.cboe.
20.2020.cboe. CNAME da50c0c184a299fe43676b236243f374.<shortened output>.bba9900e6ffeda86ff4aefde3fd61169.2020.cboe.
8.2020.cboe. CNAME 30c279b48d3a336b50f3c68997cdfcfe.<shortened output>.8cfdc7f1cdd521c73fc13f373fe4faa1.2020.cboe.
pop.2020.cboe. CNAME www.2020.cboe.
21.2020.cboe. CNAME deb82eabfcfa2e7cc0cec9646656eacf.<shortened output>.865278cdc9fce9a5359474aec557bc5a.2020.cboe.
24.2020.cboe. CNAME 07c2d74ccd9f6ed203154d54ce1f3b33.<shortened output>.a39589de5bf323c9edbab05c78749189.2020.cboe.
25.2020.cboe. CNAME db8c13dad86974dc38f86e0cf887ac2a.<shortened output>.13ebd2bf9a696c2077c05d9c36e38ae5.2020.cboe.
26.2020.cboe. CNAME 177d3373c4109ce2a7ace4f0c78e48de.<shortened output>.d8150f6596acec401bbb2d12f2f9cab3.2020.cboe.
27.2020.cboe. CNAME c1e53f4174c53bff18672b8810cd5eef.<shortened output>.5deecb6c61e3bf2e0b8ab0d1a16f3a82.2020.cboe.
28.2020.cboe. CNAME ad252e7d202df19be0a2e990cff3bf6a.<shortened output>.27f1bf365ad3bb8809a8e11518c549ad.2020.cboe.
29.2020.cboe. CNAME a1ca908d529634cc74b5b65c92095c2e.<shortened output>.90d00e198538fc682eeba62c1e283d38.2020.cboe.
3.2020.cboe. CNAME affa78e44dcf18004081fc2dbea344bc.<shortened output>.4fc8b29fd50d4b37d50080f3afbf36f1.2020.cboe.
30.2020.cboe. CNAME 951bddaf5e16c96bdced599e8286ea45.<shortened output>.a82e274d382bcde5ea920caf58dbc218.2020.cboe.
31.2020.cboe. CNAME f642753aaf74ee4670c1f20acfaf5d92.<shortened output>.1de8c6ecb4f3e57cc12f762d446248d7.2020.cboe.
32.2020.cboe. CNAME aa55754adba625ae23a86a8d5c1fc2e4.<shortened output>.65ce0128baa85eac6de4711e06bb60f4.2020.cboe.
33.2020.cboe. CNAME 69238d866a68a909aa41be1d7f21c9ba.<shortened output>.24eceb84fa1af43c8a6e70fdbe9add33.2020.cboe.
34.2020.cboe. CNAME b2c2f331a6dd81a1a7c0b4dd0a530c43.<shortened output>.0e377f44d2cf79dfcacdef619bec69ac.2020.cboe.
35.2020.cboe. CNAME d6b7bb4dd6f71e732d124e9393ebd5df.<shortened output>.e4ce1cf0388b5112257778bb9157dbfc.2020.cboe.
36.2020.cboe. CNAME df617b3aa0138fa45cc42c5a32e24ac0.<shortened output>.313b7bf7f986b78ada205648c9b875b9.2020.cboe.
37.2020.cboe. CNAME d0ab0117aee348f278fe8ebb84532ac0.<shortened output>.d64f4557c34611d14fac64c0737f863b.2020.cboe.
38.2020.cboe. CNAME b514ca39a28d70e255fb09562b6d6c42.<shortened output>.fb5778736e8df5697706a4a3f0b58b96.2020.cboe.
39.2020.cboe. CNAME 40d759ab67866d2d4c6e3d7b7ac44b68.<shortened output>.f5f540194b57151e75c0685ba2318e96.2020.cboe.
40.2020.cboe. CNAME 191e3b8a7dea44f812f2cd881765390f.<shortened output>.01d5b0f8b9c336c175533f972ecdae7c.2020.cboe.
41.2020.cboe. CNAME 3bd11a750a12d13c7ea562881e0de8c5.<shortened output>.8e02a4f0d76474062fa3d8cdd61893f1.2020.cboe.
42.2020.cboe. CNAME f10c19f007ce5c0e70eed1fff0ff0a7d.<shortened output>.ec6d21d71baefd9efa1f24287436900f.0000.2020.cboe.
server2.2020.cboe. A 10.10.10.20
6.2020.cboe. CNAME 40fa9ff20ccff01b9a98c8145f162112.<shortened output>.dd491de1c7046df8eb6d8d9b5a45d38a.2020.cboe.
ftp.2020.cboe. A 10.20.30.10
11.2020.cboe. CNAME ca2526ca9358412590fdf245bb6e5547.<shortened output>.1f17a2adc625329203e39038a1e8905a.2020.cboe.
10.2020.cboe. CNAME b6c999807fdcfa7e3865c82e3574d1ea.<shortened output>.640ee5951f5b0c26ecbfdf3eb8bae1b1.2020.cboe.
server.2020.cboe. A 10.10.10.1
server1.2020.cboe. A 10.10.10.10
webmail.2020.cboe. A 10.30.10.12
imap.2020.cboe. CNAME www.2020.cboe.
22.2020.cboe. CNAME 17c23030293142ebcacb95d717c5612c.<shortened output>.9c4cfca69cef289e3187277eac1e4e4f.2020.cboe.
23.2020.cboe. CNAME 54838d0785455cab15870d1cd98ca39a.<shortened output>.182250a915c23c542117d9a1dbf54113.2020.cboe.
server3.2020.cboe. A 10.10.10.30
smtp.2020.cboe. CNAME www.2020.cboe.
Extract all 1-42 CNAME records, sort them, remove domain part and dots. Convert to dns.bin file.
$ for i in $(seq 1 50); do dig $i.2020.cboe @10.1XX.1YY.113 +short; done | sed -e 's/.2020.cboe.//' | tr -d '.' | xxd -r -p > dns.bin
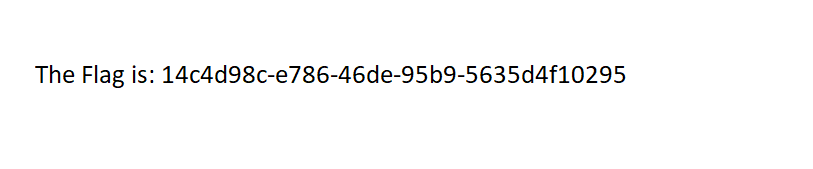
File dns.bin is a gzip archive, which contains a PNG picture. Extract it.
$ file dns.bin
dns.bin: gzip compressed data, last modified: Mon Nov 9 09:50:59 2020, from Unix, original size modulo 2^32 3984
$ gzip -dkc dns.bin | file -
/dev/stdin: PNG image data, 813 x 169, 8-bit/color RGB, non-interlaced
$ gzip -dkc dns.bin > dns.png
The image contains the flag.